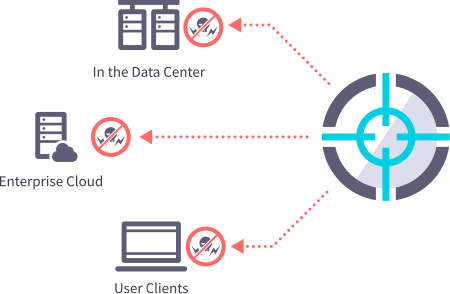
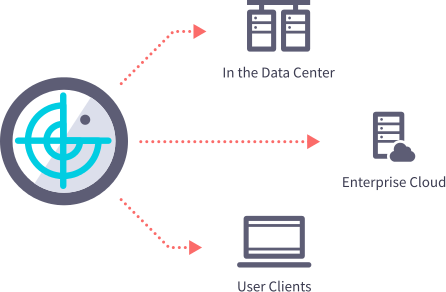
We protect enterprise client devices, data centers and cloud deployments from cyber-attacks. Organizations use our holistic security approach to eliminate silent security failures in unmanaged devices, reduce non-compliant assets, protect endpoints against known and unknown threats, and investigate and implement corrective actions for identified breaches.
Ziften Zenith
Zenith enables – unmanaged IT asset discovery, system monitoring and hardening, threat detection and hunting, incident response and containment, and deep lookback forensics to protect organizations from cyber-attacks.


Ziften ZFlow
ZFlow generates an extended version of NetFlow to uniquely provide last-mile network visibility for all endpoint network activity. See what you are missing at the edge of your network and in the cloud.
Assess
With the Assess service, Ziften continually monitors and provides your organization with strategies for improving your security posture and oversight to ensure proper implementation of security controls and programs.
Hunt
With the Hunt service, Ziften helps continually monitor and proactively hunt for issues and threat adversaries in your environment – immediately exposing these issues and threats so they do not dwell and/or spread.
Respond
With the Respond service, Ziften applies tried and true process and expertise to confirm and prioritize the threat, stop the adversary in its tracks, and uncover and remediate the full extent of the issue.